I recently posted about a security problem caused by the “same origin” of the iframe that is used on the preview window of the the page builder: /topics/possible-security-hole-in-unbounce
The Unbounce team is still fixing that - but the problem is deeper than just that.
The Unbounce app allows users to upload and download custom made templates by any one - that includes all the template elements also custom JS scripts - this fact forces Unbounce to follow some strict security protocols concerning JS:
- Sandboxing js - execution only in preview page.
- No custom script execution inside the builder page.
The first one is problematic and is discussed in the first post mentioned above. The second one is vulnerable two 😕
First, the reason there should not be any script execution in the builder is because a template author may include a script that steals your cookies with your emails, session token etc… and can log as the uploader to his account and : change passwords, steal content, steal leads etc…
I found two ways (may be more) to create a template with a script that will execute immediately when the user enters the builder page:
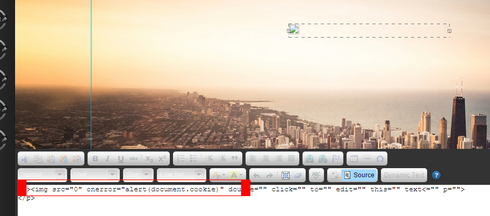
Injecting the script through the text editor:
The editor don’t allow you to include none text elements or add scripts to the text source HTML code, but it allows inline js on text elements such as
As you can see this is fully supported by the text editor and will be saved in the page builder DOM - normally text editors filters elements attributes but not in this case.
**
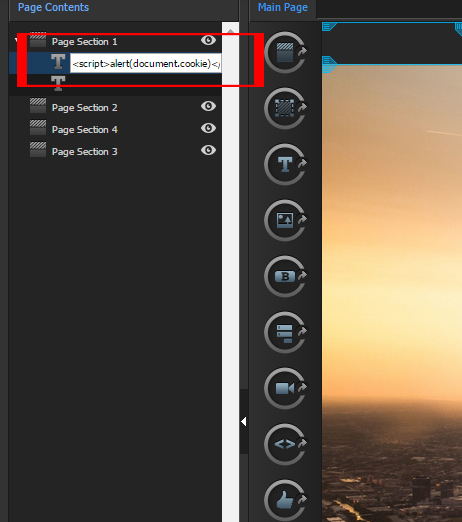
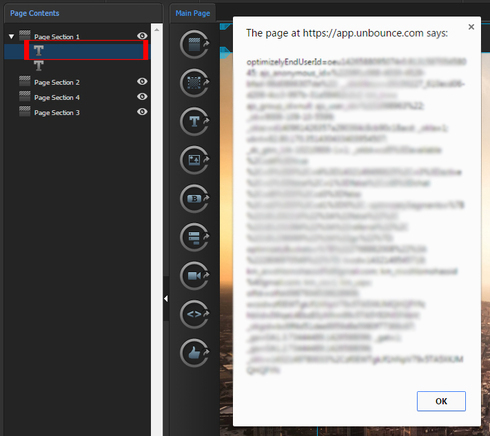
Injecting the script through the elements name: **
Even easier than using the editor is injecting scripts directly to the elements titles (in the tree view on the left) - Most of the “name displaying” elements in the Unbounce app escape HTML tags but not in this case:
 Those are pretty serious issues since Unbouce is getting bigger and a lot of users are seeking for new templates and even purchasing them. An attacker can easily exploit those weaknesses to take over accounts and causing harm to commercial users and private users.
Those are pretty serious issues since Unbouce is getting bigger and a lot of users are seeking for new templates and even purchasing them. An attacker can easily exploit those weaknesses to take over accounts and causing harm to commercial users and private users.
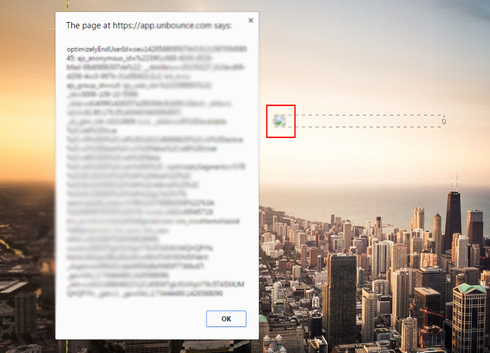
Consider that a script embedded in a template that will execute immediately when the use clicks the “edit” button can send data easily using ‘XMLHttpRequest’ object in a quick line of code and there are several more ways to hijack the cookies and user information once you can execute the scripts.
Your thoughts please.